Setup a home VPN server and access your private network from anywhere
Hosting a VPN at home offers several benefits such as allowing you to access all of your devices and personal web services from anywhere and protecting your communications when connecting from an untrusted or low-security infrastructure.
A Raspberry Pi is well suited to the task with its low-energy consumption and high reliability.
OpenVPN installation and setup
I suggest to follow the instruction from Digital Ocean available in this post that will allow to deploy a VPN server on a Raspberry Pi.
Dealing with changing IPs
One major problem you may encounter is that your ISP might randomly (and will probably at some point) change the public IP of your home router. As a result, when a devices tries to connect to your VPN server, it is unable to do so as it cannot find the server.
A simple fix is to register a domain name that you can use to point to your current IP address. Any change in IP address will then be reflected in the DNS record to make sure it always points to the correct and latest valid IP address. If you do not want to pay for such a service, I recommend using DuckDNS to register a subdomain of duckdns.org.
You can automate the check and IP updates by using the script provided on the duckdns website (just follow the instructions on the duckdns website in the “install” tab when you’re logged in).
Configuring Pi-Hole
If you’re using Pi-Hole as your home DNS server, follow the instructions from pi-hole’s website to make it your OpenVPN DNS resolver. This will make all DNS requests pass through your Pi-Hole and clean-up your internet traffic, wherever you’re connected. Pretty neat!
Adding security
The installation of OpenVPN gives you access to your home network but can potentially open a breach for attackers directly into your home. Be careful with what you do and make regular security checks.
Below are a few tools you can use to protect yourself against attacks and to monitor the successful and failed access to your VPN.
fail2ban
fail2ban is a python-based intrusion prevention software framework that protects computers from brute-force attacks. You can configure it to log and block every failed attempt to connect to OpenVPN. In order to do this, you need to create a new rule.
Create the new file openvpn.local
vim /etc/fail2ban/filter.d/openvpn.localand add the following lines inside it. This will allow fail2ban to scan your OpenVPN logs and recognize failed connection attempts:
# Fail2Ban filter for selected OpenVPN rejections
[Definition]
failregex = [a-b]*ovpn-server.*:.<HOST>:[0-9]{4,5} TLS Auth Error:.*
[a-b]*ovpn-server.*:.<HOST>:[0-9]{4,5} VERIFY ERROR:.*
[a-b]*ovpn-server.*:.<HOST>:[0-9]{4,5} TLS Error: TLS handshake failed.*
[a-b]*ovpn-server.*:.<HOST>:[0-9]{4,5} WARNING: Bad encapsulated packet length from peer
#[a-b]*ovpn-server.*:.<HOST>:[0-9]{4,5} Connection reset, restarting \[[0-9]{1,2}\]
ignoreregex =
then edit the fail2ban configuration file:
vim /etc/fail2ban/jail.localand edit it to contain these lines to filter for failed ssh connections and openvpn connections:
[DEFAULT]
# Ban hosts for 1 hour after they perform 3 failed login attempts within 20 minutes
bantime = 3600
findtime = 1200
maxretry = 3
[sshd]
# Enables the sshd jail
enabled = true
[openvpn]
# Fail2Ban configuration fragment for OpenVPN
enabled = true
port = 655
protocol = tcp
filter = openvpn
logpath = /var/log/syslog
In the default section, you can choose how long you want to block potential attackers, how long fail2ban should keep track of failed attempts and how many retries a user gets. Beware that you might also unexpectedly block yourself out of your server.
logwatch
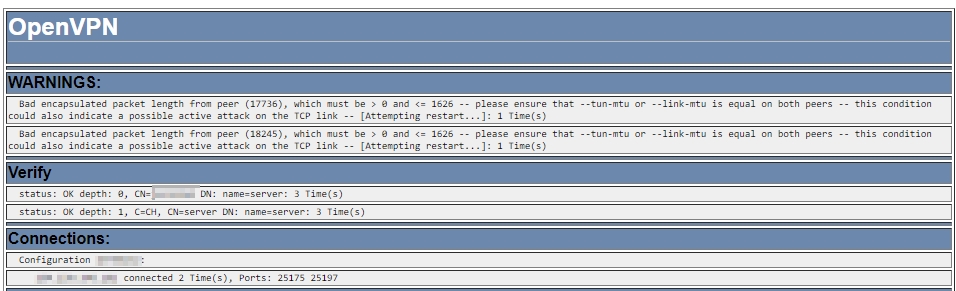
Logwatch is a powerful and versatile log parser and analyzer designed to give a unified report of all activity on a server, which can be delivered through the command line or email. By default logwatch will read your openvpn log and report every failed and successful connection attempts.
You can install it directly from the command line using the package manager:
sudo apt-get install logwatchto run a logwatch job on a daily basis, create a file in your cron.daily repository:
vim /etc/cron.daily/00logwatchand add the following content, customizing the level of details you wish and the location of the output file.
#!/bin/bash
#execute
/usr/sbin/logwatch --detail high --format html --range "since 4 days ago" --filename <PATH_TO_YOUR_FAVORITE_LOCATION>/logwatch_output.htmlThis will configure logwatch to generate an html file every morning containing a summary of your logs for the last 4 days and allow you to survey what is happening on your server.

Optional: Connecting to a second VPN
If you would like another layer of privacy and use an outgoing VPN connection from your OpenVPN server (as opposed to your normal ISP network connection), have a look at the detailed instructions in this previous post, section “Add rules to forward a second OpenVPN traffic”.